Things from Me
Happy Friday everyone!
Welcome to the newly renamed and re-logo’d newsletter!
As I’ve mentioned in the last couple newsletters, this week marks the full newsletter revamp where the original Security Copilot weekly newsletter is now part of this community. And, since this newsletter is now much, much more than just SIEM and XDR, a name change was also warranted.
So, welcome everyone to the “THE PROMPT for Microsoft Security” weekly newsletter. It’s the same concept as before where each week you get a blast of all the new things from Microsoft and the security community, but now with a new name that is better aligned with all the happenings at Microsoft.
…
All that said, the newsletter is taking a Brief Hiatus for an Exciting European Speaking Tour!
As the summer kicks into high gear, I'll be taking a short two-week break from the newsletter while I embark on a whirlwind speaking tour across Europe. First up: Workplace Ninjas in Oslo the week of June 9th, followed by Workplace Ninjas UK in Edinburgh the week of June 16th. I'm beyond excited to share insights, exchange ideas, and connect with attendees from across the industry.
But the break won't last long—I'll be back in your inbox on June 27th, ready to pick up right where we left off. And looking ahead, I'm in the process of formalizing a fantastic opportunity for my next European trip: a keynote for the AI Security Summit in London this November! If you're attending or would like to connect, I'd love to hear from you. Check out the summit details here: securitysummit.ai.
…
That’s it from me for this week.
We’ll talk soon.
-Rod
Things to Attend
Things that are Related
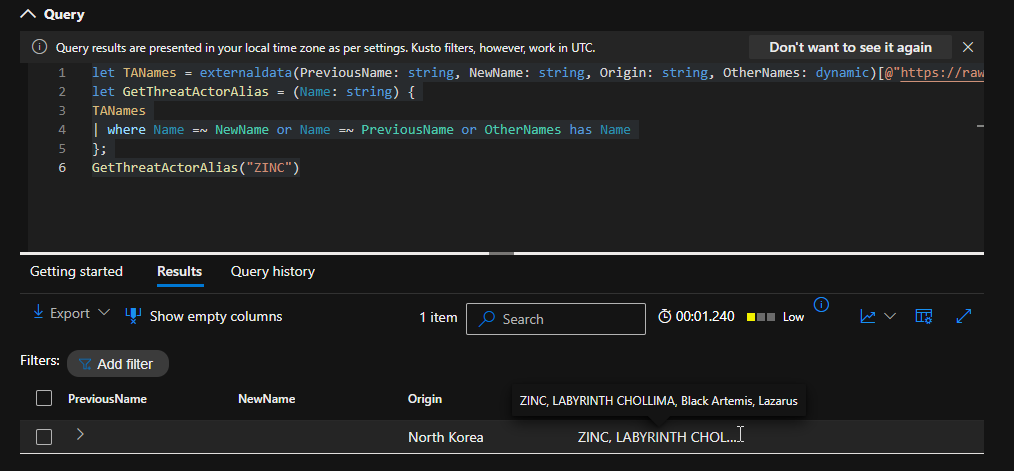
Use the following query on Microsoft Defender XDR and other Microsoft security products supporting the Kusto query language (KQL) to get information about a threat actor using the old name, new name, or industry name.
https://learn.microsoft.com/en-us/unified-secops-platform/microsoft-threat-actor-naming#resources
Things to Watch/Listen To
Things in the News
Announcing a new strategic collaboration to bring clarity to threat actor naming - …that’s why we are excited to announce that Microsoft and CrowdStrike are teaming up to create alignment across our individual threat actor taxonomies. By mapping where our knowledge of these actors align, we will provide security professionals with the ability to connect insights faster and make decisions with greater confidence.
Security Copilot Things
Using parameterized functions with KQL-based custom plugins in Microsoft Security Copilot - Microsoft Security Copilot offers customers great flexibility to bring custom insights into Security Copilot sessions using custom plugins. KQL-based plugins are commonly used to tap into data stored in Microsoft Sentinel Log Analytics workspaces, Microsoft Defender XDR Advanced Hunting tables and Azure Data Explorer clusters to bring insights into a Security Copilot session. KQL-based user-defined functions are supported across these three platforms and offer significant advantages for querying and analyzing large datasets. These benefits include the ability to encapsulate reusable logic, enhance query efficiency, and improve maintainability.
Microsoft Sentinel Things
Ultimate Health Check For Microsoft Sentinel: Boost Security & Savings - A robust Microsoft Sentinel deployment is more than just a "set and forget" cloud SIEM solution. As your organization's security posture evolves, so too do your data sources, threat models, and cost considerations.
Automating Microsoft Sentinel: Part 2: Automate the mundane away - Learn how to use automation tools and techniques to make your security operations awesome right away with Microsoft Sentinel.
Detecting Suspicious Activities in Microsoft Sentinel: Writing Threat-Hunting Queries Using KQL - Microsoft Sentinel is a powerful cloud-native Security Information and Event Management (SIEM) solution that empowers organizations to detect, investigate, and respond to security threats. One of its core strengths is the ability to perform proactive threat hunting using Kusto Query Language (KQL). By writing effective KQL queries, security analysts can uncover suspicious activities, identify potential threats, and strengthen their organization's security posture. In this blog post, we'll explore how to write threat-hunting queries in Microsoft Sentinel using KQL, with practical examples and best practices.
Defender for Cloud Things
Performing Advanced Risk Hunting in Defender for Cloud - Microsoft Defender for Cloud's Cloud Security Explorer provides security teams with an intuitive visual interface to investigate their cloud security posture. It excels at helping users explore relationships between resources, identities, permissions, and vulnerabilities while surfacing potential misconfigurations and risky assets that could be vulnerable to attacks and breaches. But what happens when you need to go deeper than what the UI can offer?
Defender for Endpoint Things
Discover how automatic attack disruption protects critical assets while ensuring business continuity - Microsoft Defender developed automatic attack disruption: a built-in self-defense capability that identifies & disrupts multi-domain attacks in near real time to prevent further damage across the organization. We recently announced how we protect domain controllers against ransomware as the latest attack disruption innovation.
How Microsoft Defender for Endpoint is redefining endpoint security - The likelihood of a Microsoft Defender for Endpoint customer getting encrypted over the past 18 months has also decreased by 300%. Microsoft disabled and contained 120,000 compromised user accounts and saved more than 180,000 devices in the last six months alone.
Defender XDR Things
Expanding the Identity perimeter: the rise of non-human identities - With the rise of cloud applications and AI, machine-to-machine access and authentication has become even more prevalent. From automating workflows, integrating applications, managing cloud services and even powering AI agents, non-human identity (NHI) has become vital to modern work. These digital constructs come in many different varieties, each with their own unique characteristics, but because they are foundational elements of many critical business processes, they represent a prime target for cyber-criminals.
Microsoft Entra Things
Privileged Identity Management + Just-in-Time Access: Grant Access Only When It’s Needed - As a nonprofit, you’re on a mission—serving communities, driving change, and making every dollar count. The last thing you need is a security breach or an IT mess slowing you down. But here’s the truth: giving people always-on admin access (even if it’s just “easier for now”) opens the door to accidental mistakes or worse—cyberattacks.
Entra ID groups inspector: a Log Analytics dashboard for tracking changes to groups - In this post I will show you a Log Analytics dashboard allowing you to monitor Entra ID groups. You can see group created or removed, members added in a group or removed from a group and owners added on a group or removed from a group.
Putting the “Identity” in Identity Threat Detection and Response with Microsoft Entra ID - In the latest Secure Employee Access report, we reveal the need for unified access and security tools. The mix of tools create disjointed security strategies, which cause a 79% increase in breaches and operational challenges. Native, comprehensive protection is key to securing identities—the capabilities and integration between Microsoft Entra ID and Microsoft Defender XDR simplify the tools SOC and Identity teams need in their identity management and threat hunting toolbox.
Understanding and Mitigating Golden SAML Attacks - In this blog, we’ll explain how Golden SAML attacks work and what you can do to protect against them, with a particular focus on how they can impact Microsoft Entra deployments.