Microsoft Sentinel this Week - Issue #144
Stuff from Me
Happy Friday, everyone!
It’s me again. Thanks for inviting me into your inbox each week. It’s hard to explain the true appreciation of your interest in the topics covered in this newsletter, but your readership and engagement is a powerful thing that helps us build better products and enables this community to be builders and creators.
So, thanks so much for your continued partnership.
…
I’m fresh back from NYC for the latest leg of the Microsoft AI Tour. NYC was even more fantastic than the San Francisco event (if you can believe that). We had roughly 4500 people attend. I could be wrong, but I believe there were around 1500 for San Francisco.
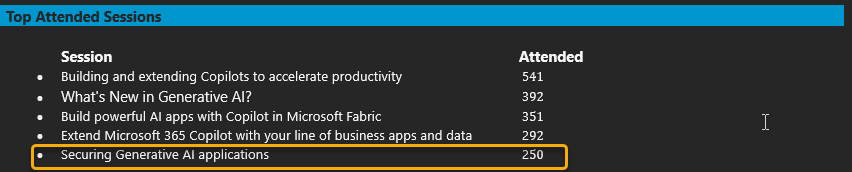
The biggest success of the day to me was that my tiny little session on Securing Generative AI Applications was the 5th most attended session, with many supplying feedback that it should have been longer, and they wanted more.
This is a session without any of the fancy AI demos that the others have. It’s just me. Talking about security and AI.
To me that’s a true vindication of the last year and half of things I’ve worked on. The audience was split between developers and operations/security roles. It warms my heart to see developers interested in the security discussion. The Microsoft AI Tour is an awesome event, and you should definitely attend this free event if one of the upcoming dates makes it near you. Check out all the dates here: https://envision.microsoft.com/
The next dates in the tour are being delivered by a couple of my teammates, Joylynn Kiriu for Bengaluru, India and Sarah Young for Sydney, Australia, so I get travel rest for month of February which works out great because there’s Copilot for Security training coming soon.
…
Registration for our 2nd annual Microsoft Secure is live! The event runs Wednesday, March 13, 2024 | 9:00 AM-11:00 AM Pacific Time (UTC-7), and will introduce, well…let’s just say you don’t want to miss the announcements for the day.
Register for this virtual event here: https://mssecure.eventcore.com/
…
I mentioned a few times in the newsletter already that I will be traveling to Europe in March to participate in the first-ever Experts Live in Denmark.
Well, the event’s session schedule is now live: https://events.justattend.com/events/conference-sessions/584b32f5
If you’re in the area, or plan to be, it will be awesome to meet many of this community in-person!
Registration is here: https://events.justattend.com/events/conference-tickets/584b32f5
…
That’s it for me for this week. I hope your weekend and week ahead are fabulous.
Talk soon.
-Rod
Stuff to Read
Multi-Tenant Applications Detections - Discussing various Sentinel and Microsoft XDR detections related to multi-tenant applications, including the ones that are possible and the ones that are not.
Complex Sentinel Deployments Using ARC and AMA Over Private Links and Private Endpoints - Managed Sentinel - Large organizations sometimes opt for an architectural choice to use private links and private endpoints in the context of ingesting data from on-premise servers into Microsoft Sentinel.
Microsoft Sentinel: Your First Instance - In our previous blog post, “Introduction to Microsoft Sentinel,” we embarked on a journey into the core concepts, benefits, and components that make Microsoft Sentinel a formidable SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response) solution. If you haven’t yet read the introduction, I highly recommend doing so to gain foundational insights before diving deeper into today’s, ‘Create Your First Microsoft Sentinel Instance’.
Microsoft Sentinel: Malicious Inbox Rule V2 – Prof-IT Services - This improved Sentinel Analytics Rule can be used to detect malicious Inbox Rules used by threat actors to hide invoice fraud activity. I’ve used the Inbox rule currently available as a template within Sentinel and modified it to alert on Outlook rules I encountered in the wild.
Create Analytic Rules To Query External Data In Microsoft Sentinel - Azure Data Explorer (ADX) and Azure Blob storage have long been recommended as long-term archival solutions for Sentinel. Microsoft recommended using ADX and Blob storage for long term retention, and the good news is that Azure Monitor lets you query data externally from your Log Analytics workspace for a full SOC experience.
SOC – Testing Microsoft Sentinel Analytic Rules At Scale - This article shows our main challenges during the development of our test framework and how we solved them. In technical terms: we demonstrate a test method for Microsoft Sentinel’s (KQL) Analytic rules, utilizing Python’s built-in unittest framework, based on a Terraform plan.
Enable your key business needs within Microsoft Sentinel with step-by-step guidance - Modernize your security operations center (SOC) with Microsoft Sentinel. Uncover sophisticated threats and respond decisively with an intelligent, comprehensive security information and event management (SIEM) solution for proactive threat detection, investigation, and response.
How to Deploy Microsoft Sentinel Effectively - Microsoft Sentinel is a cloud-native security information and event management (SIEM) solution that helps organizations detect, investigate, and respond to cyber threats. Sentinel leverages the power of artificial intelligence, machine learning, and automation to provide a comprehensive and scalable security platform. However, to get the most out of Sentinel, organizations need to follow some best practices for deploying, managing, and using it. In this article, we will share some insights on how to optimize your Sentinel deployment and maximize its benefits.
Stuff to Attend
Stuff That's New or Updated
AWS and GCP data connectors now support Azure Government clouds - Microsoft Sentinel data connectors for Amazon Web Services (AWS) and Google Cloud Platform (GCP) now include supporting configurations to ingest data into workspaces in Azure Government clouds.
The configurations for these connectors for Azure Government customers differs slightly from the public cloud configuration. See the relevant documentation for details:
Connect Microsoft Sentinel to Amazon Web Services to ingest AWS service log data
Ingest Google Cloud Platform log data into Microsoft Sentinel
Stuff That's Related
Migrating from the Azure MMA to AMA Agent - I have another conversation about the sunset of the Microsoft Monitoring Agent (MMA). Back on November 13, 2023 I posted and article on how to do a bulk removal of the Azure MMA agent, but before you can remove the MMA agent you need to have the AMA agent ready to take over the work. Below are details to assist in this endeavor.
Stuff About Security Copilot
Intune & Security Copilot better together | LinkedIn - In the last couple of weeks, I have been able to test and review the Security Copilot capabilities when it comes to Microsoft Intune. Security Copilot is Microsoft’s security solution that uses generative AI to assist security professionals in enhancing their security performance at a fast and large scale, while following the ethical standards of AI.
Stuff in Techcommunity
Sentinel not ingesting all Office 365 logs from Exchange - Recently starting using Sentinel and we're ingesting Office 365 logs using the Microsoft 365 (formerly, Office 365) version 2.0 connector.
Extract a field & append to URL - Can I extract a field from a log and then append that to a URL? In the example query I want to have the ID field appended to the URL.
Thanks for reading Microsoft Sentinel this Week! Subscribe for free to receive new posts and support my work.