Things from Me
Happy Friday, everyone!
It’s me again. Thanks for inviting me into your inbox each week. It’s hard to explain the true appreciation of your interest in the topics covered in this newsletter, but your readership and engagement is a powerful thing that helps us build better products and enables this community to be builders and creators.
So, thanks so much for your continued partnership.
…
I’m fresh back from NYC for the latest leg of the Microsoft AI Tour. NYC was even more fantastic than the San Francisco event (if you can believe that). We had roughly 4500 people attend. I could be wrong, but I believe there were around 1500 for San Francisco.
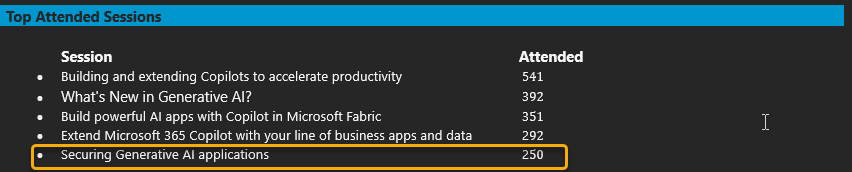
The biggest success of the day to me was that my tiny little session on Securing Generative AI Applications was the 5th most attended session, with many supplying feedback that it should have been longer, and they wanted more.
This is a session without any of the fancy AI demos that the others have. It’s just me. Talking about security and AI.
To me that’s a true vindication of the last year and half of things I’ve worked on. The audience was split between developers and operations/security roles. It warms my heart to see developers interested in the security discussion. The Microsoft AI Tour is an awesome event, and you should definitely attend this free event if one of the upcoming dates makes it near you.
Check out all the dates here: https://envision.microsoft.com/
The next dates in the tour are being delivered by a couple of my teammates, Joylynn Kiriu for Bengaluru, India and Sarah Young for Sydney, Australia, so I get travel rest for month of February which works out great because there’s Copilot for Security training coming soon.
…
Registration for our 2nd annual Microsoft Secure is live! The event runs Wednesday, March 13, 2024 | 9:00 AM-11:00 AM Pacific Time (UTC-7), and will introduce, well…let’s just say you don’t want to miss the announcements for the day.
Register for this virtual event here: https://mssecure.eventcore.com/
…
I mentioned a few times in the newsletter already that I will be traveling to Europe in March to participate in the first-ever Experts Live in Denmark.
Well, the event’s session schedule is now live: https://events.justattend.com/events/conference-sessions/584b32f5
If you’re in the area, or plan to be, it will be awesome to meet many of this community in-person!
Registration is here: https://events.justattend.com/events/conference-tickets/584b32f5
…
That’s it for me for this week. I hope your weekend and week ahead are fabulous.
Talk soon.
-Rod
Things to Attend
Things to Watch/Listen To
Things in Techcommunity
User Audit Logs - Compromised Computer Help - I had a user MS credentials used to login remotely. Account is stable now but as I go through logs for the time, I believe the user gave up their password. We fond in the user audit log a modified permission.
ATP sensor fails to start since yesterday - we run the ATP sensor with a gMSA account on all domain controllers. Yesterday we restarted all machines because of January patch day and now the ATP sensor will get stuck while starting.
Things that are Related
Security Copilot Things
Intune & Security Copilot better together | LinkedIn - In the last couple of weeks, I have been able to test and review the Security Copilot capabilities when it comes to Microsoft Intune. Security Copilot is Microsoft’s security solution that uses generative AI to assist security professionals in enhancing their security performance at a fast and large scale, while following the ethical standards of AI.
Defender for Cloud Things
Bridging the Gap Between Code and Cloud with Defender for Cloud - Microsoft Defender for Cloud addresses this critical need with its container mapping feature. This blog post explores how Defender for Cloud streamlines the process of tracing vulnerabilities in container images back to their origins in CI/CD pipelines, specifically within Azure DevOps and GitHub environments. This functionality is key to facilitating effective developer remediation workflows, thereby enhancing the security posture of cloud-native applications.
Microsoft Purview Things
Microsoft Purview now supports Availability Zones - Microsoft purview for governance experiences has enabled partial support for availability zones in certain regions and services. The availability zone support would continue to expand to accommodate more regions and services.
Scan Microsoft Fabric Items in Microsoft Purview - Previously we have announced the Public preview for Microsoft Fabric Items in Microsoft Purview and starting from December 13th 2023, scanning Fabric tenants registered with the Fabric data source in Microsoft Purview will capture metadata and lineage from Fabric items including Power BI. The new feature is available in all Microsoft Purview public cloud regions.
Considerations for deploying Microsoft Purview data security and compliance protections for Microsoft Copilot - Microsoft Copilot for Microsoft 365 has the capability to access data stored within your Microsoft 365 tenant, including mailboxes in Exchange Online and documents in SharePoint or OneDrive.
Microsoft Entra Things
Introducing More Granular Certificate-Based Authentication Configuration in Conditional Access - I’m thrilled to announce the public preview of advanced certificate-based authentication (CBA) options in Conditional Access, which provides the ability to allow access to specific resources based on the certificate Issuer or Policy Object Identifiers (OIDs) properties.
Weird issues with Entra ID Signin Logs - I recently experienced an issue where a Sentinel alert for successful Entra ID signin from an unexpected location, fired multiple times after an attacker had already been evicted, and all sessions had been revoked. Initially I assumed something had gone wrong with the revocation process, as all of the subsequent signin events showed an existing token granted access without need for MFA/Password - "MFA requirement satisfied by claim in the token".
AzCopy support for Entra ID authentication - Using AzCopy version 10.22.0 or newer you can reuse your existing Entra ID authentication tokens from Azure PowerShell and Azure CLI for authentication for blob transfers to and from your storage accounts. This will reduce the number of times you have to enter your credentials when using Azure PowerShell and Azure CLI in the same session as you login to either Azure PowerShell or Azure CLI once and you do not need to enter a separate set of credentials in AzCopy. By the end of this article, you will be able to authenticate AzCopy actions seamlessly on Linux or Windows by reusing an existing OAuth token.
Microsoft Entra ID Role vs Azure Role | LinkedIn - The article discusses about the difference between Microsoft Entra ID roles and Azure roles - and why it is important to know them.
How to Report App Credential Expiration with PowerShell - A reader asks if it’s possible to notify administrators when app secrets expire or are close to expiring. App secrets (also called client secrets) are a mechanism to allow Entra ID registered applications to prove their identity and secure an access token to allow them to retrieve data. App secrets last between three and twenty-four months are not intended for production use. Instead, app secrets are a good way to test an application to make sure that it can access the right data using the right permissions before moving it from development to production.