Things from Me
Happy Friday everyone!
It’s been an awesome couple weeks since our last newsletter issue.
I had mentioned previously that I gave up trips to Paris and Berlin due to my new granddaughter close to being born. But she had other ideas. Instead, I woke on Wednesday of last week in Denmark to see texts from my wife that the baby had waited until I was away. But it worked out in that I was able to make the birth announcement in my Copilot for Security keynote, including birth pictures.
So, here’s my announcement to all of you. Welcome to Meredith Eloise Rumker! Here’s a great picture. You can tell my grandboy loves her already. My wife and I sure do.
Experts Live in Denmark was an awesome event and I thoroughly enjoyed connecting with everyone in-person. But my best memories are hanging with my good friends Morten Waltorp (and his wife) and Henrik Wojcik, who I’ve come to know over the last few years through the Microsoft MVP program. They welcomed me to the area with open arms and good times. I also appreciate the Experts Live crew for having me.
…
Can you believe GA for Copilot for Security is this Monday??!!
April 1st marks the end of one journey, but the beginning of another. And you’ll see this week’s newsletter issue has a LOT of Copilot for Security content, but that’s sort of a given considering the general release is so close. I noted a while ago that a Copilot for Security specific newsletter was not necessary, but that my not be the case for much longer. Stay tuned.
As we get closer to GA for Copilot for Security, I'll be hustling to post additional prompt samples that you can use. https://aka.ms/CfSPromptLibrary
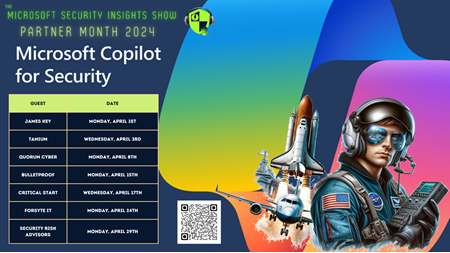
And The Microsoft Security Insights Show will be hyper-focused on Copilot for Security partners next month. We hope you can join live, but definitely subscribe and listen after if that works best for you.
Click the image to check out next month’s schedule:
Additionally, as part of the Copilot for Security GA event, myself and my MSI Show co-hosts will be delivering a couple webinars to dig deep into working with the new service.
See: Learn Live: Get started with Microsoft Copilot for Security
…
That’s it from me for this week.
Talk soon.
-Rod
Things to Attend
Copilot L33t Sp34k is a webinar series that covers generative AI and Microsoft Copilot for Security. As the webinar name alludes (L33t Sp34k definition), this series was crafted for an experienced security professional audience that wants to hear industry experts talk broadly about how to use AI securely and how organizations should use AI, like Microsoft Copilot for Security, to enhance their security. This series is hosted by Sarah Young, and each episode will feature guest(s) both internal and external to Microsoft. Register: https://learning.eventbuilder.com/CopilotL33tSp34kSeries
Things in Techcommunity
Huge difference between Defender overview and Graph explorer Kusto - In Defender overview going to recommendation or posture, we have something completely different when we use the Kusto in graph explorer as indicated.
Defender and Azure Devops reporting - I have configured defender for our Azure Devops Organization and we have some details when we visit MS defender | Devops.
Copilot for Security Things
Copilot for Security is not an oxymoron – it's a potential game-changer for security-starved businesses - Picture this: you're a brand-new security operations coordinator at a major company that's been hit with dozens of daily ransomware attack attempts. You need to analyze, understand, and develop a threat defense plan – and all on your first day.
Microsoft’s ‘Copilot for Security’ brings generative AI to the frontlines of cybersecurity - Vasu Jakkal, Microsoft’s corporate vice president for security, emphasized the significance of this release in a recent interview with VentureBeat. “GenAI is a superpower that security needs right now,” she said. “If you step back and look at the threat landscape and what we’re up against, in just the last year, the speed, the scale, and the sophistication of attacks has increased pretty dramatically.”
Demystifying Security Copilot Features & Licensing - Many have questions about the costing model, how much it will cost to have it in the tenant, and minimum licensing requirements. I have simplified it below. I had the privilege of speaking with one of the partners facilitating the Security Copilot rollout in many companies.
Tanium + Microsoft Copilot for Security: revolutionizing cybersecurity - Combine complete endpoint visibility and control with purpose-built AI capabilities to enhance defenses and mitigate threats.
Copilot for Security - script analysis integration - Copilot for Security is great: among the many capabilities it offers (KQL query in natural language, incident summary and reporting, Threat Hunting with Threat Intelligence etc) it also allows you to analyze scripts! This can be useful from a purely descriptive perspective - what a script performs - but also from a security perspective, especially if the script is voluntarily obfuscated/encoded by the attacker.
Custom Plugins in Microsoft Copilot for Security | LinkedIn - In preparation for General Availability of Copilot for Security on April 1, 2024 I thought I would take some time to share with the community just how easy and flexible Microsoft's Copilot for Security's Custom Plugin Framework is to work with.
Brief: Adjusting Access to Custom Plugin Management in Copilot for Security - Copilot for Security provides a platform to allow developers and users to create plugins that can do specific tasks. Copilot for Security’s extensibility is one of its superpowers. Copilot for Security has many built-in plugins, but you can also make Copilot for Security do more things by adding your own plugin.
Brief: Standalone and Embedded Copilot for Security Experiences - The Standalone and Embedded experiences for Copilot for Security cater to different usage scenarios. Here’s some suggestions for where each may make sense in your organization.
Tanium Integrates with Microsoft Copilot for Security - Changing the Game for Cybersecurity Teams | Tanium - Learn how Tanium and Microsoft Copilot for Security joined forces to empower SOC teams with real-time, AI-driven security.
Copilot for Security Tip: Conserving SCUs by Utilizing Prompt History - As more organizations discover the value of utilizing Copilot for Security to augment daily security operations, they may want to identify ways to minimize SCU usage.
Brief: Copilot for Security is Two Experiences but One Connected Service - A question was raised during my Copilot for Security keynote at Experts Live in Denmark recently about since there are two different experiences, are they somehow still connected? It’s worth noting that Copilot for Security is an Azure service. In fact, the Azure portal is how it’s accessed to enable and configure in an organization’s tenant.
Get Ready for Takeoff: Microsoft Copilot for Security - Microsoft announced that the official launch day of Copilot for Security will be April 1, 2024. This proves that Microsoft won't let a late-night snowstorm stop its pursuit of security revenue or find new applications for generative AI. Approximately one year after announcing the project, Copilot for Security will be available to security leaders and their teams. We share our takeaways and thoughts on preparing security leaders for the technology below.
Defender for Cloud Things
Protect Against OWASP API Top 10 Security Risks Using Defender for APIs - Defender for APIs offers full lifecycle protection, detection, and response coverage for APIs. Defender for APIs helps you to gain visibility into business-critical APIs. You can investigate and improve your API security posture, prioritize vulnerability fixes, and quickly detect active real-time threats.
Microsoft Defender for API Security - Estimate Your Plan Cost Easily - Microsoft Defender for Cloud introduces an efficient solution with its Defender for APIs feature, designed to provide comprehensive lifecycle protection, detection, and response coverage for your APIs. Defender for APIs is designed to help you protect your APIs from OWASP top API risks and empower you with the visibility needed to enhance your API security posture. With the ability to detect real-time threats swiftly, you're always a step ahead in responding to API security threats and triage.
Some compliance features in Microsoft Defender for Cloud will be retired - Microsoft Actions and Compliance offerings, two regulatory compliance features in public preview, will no longer be available through the Defender for Cloud portal pages starting September 30, 2025.
Using Kusto to get a list of machines with vulnerabilities from Defender for Cloud | LinkedIn - How can I get the full list of machines with vulnerabilities in Microsoft Defender for Cloud?
DevSecOps with Microsoft Defender for DevOps - DevSecOps, which stands for development, security, and operations, is a framework that integrates security into all phases of the software development lifecycle. Organizations adopt this approach to reduce the risk of releasing code with security vulnerabilities.
Microsoft Defender for Storage in pills - Defender for Cloud is the Microsoft Cloud-Native Application Protection Platform (CNAPP) solution - the goal is to unify security and compliance analysis in a single platform to prevent, detect, and respond to cloud security threats.
Resource-level billing change for Defender for Servers Customers - Effective Monday, <30 days from release>, only when Defender for Servers is enabled for the resources' subscription or the subscription hosting a Connector for AWS resources:
Direct Billing to Resources: We're changing how we report your billing. Instead of using a general workspace ID, your bills will now be directly linked to each compute resource ID. This means each Virtual Machine (VM), Virtual Machine Scale Set (VMSS), Azure Arc-enabled server and EC2 Instance will have its own billing entry.
More Detailed Billing: Customers will no longer receive one large bill for all workspace resources. Starting March 11, customers will see individual costs for each of the above resources. This granular view will provide a clearer picture of what subscriptions your costs are allocated to.
AWS Specifics: For those using AWS resources, the subscription hosting the AWS Connector will be billed for the resources used.
Continuous export now includes attack path data - We are announcing that continuous export now includes attack path data. This feature allows you to stream security data to Log Analytics in Azure Monitor, to Azure Event Hubs, or to another Security Information and Event Management (SIEM), Security Orchestration Automated Response (SOAR), or IT classic deployment model solution. Learn more about continuous export.
Optimizing Azure Arc Health in AWS and GCP: A Defender for Cloud Workbook - This workbook addresses a common challenge faced by organizations deploying Defender for Server on AWS or GCP workloads. The challenge is to effectively visualize the health and availability of Azure Arc agent on AWS EC2 or GCP virtual machines. To address this, I have developed a solution using Azure Workbooks. The solution is an interactive workbook that provides view of all machines connected to Defender for Cloud, with and without Azure Arc deployment, including status and additional information.
ServiceNow integration is now generally available (GA) - We're announcing the general availability (GA) of the ServiceNow integration.
Prepare for upcoming transitions in Defender for Servers - When we released Defender for Cloud (which was formerly known as Azure Security Center) a few years back, we had to rely on Log Analytics agent for some capabilities in both, our foundational CSPM, and in our server protection offerings. In the meantime, there had been many changes especially in the Microsoft Security platform stack, and with the upcoming deprecation of this legacy monitoring agent in summer 2024, we now had the unique chance to re-evaluate our dependencies, to remove some of them while further improving our capabilities at the same time.
Defender for Endpoint Things
Further simplifying the Microsoft Defender for Endpoint onboarding experience with Microsoft Intune - Microsoft Intune is making it even easier for admins to deploy and configure Microsoft Defender for Endpoint on devices with simplified experiences for discoverability, deployment, and continuous monitoring across devices.
Microsoft Entra Things
Microsoft Entra Internet Access: Unify Security Service Edge with Identity and Access Management - At our latest Microsoft Ignite event, we announced and demonstrated new capabilities within Microsoft Entra Internet Access, an identity-centric Secure Web Gateway (SWG) solution capable of converging all enterprise access governance in one place. These capabilities unify identity and network access controls to help eliminate the security loopholes and manageability created by using multiple security solutions. This helps protect enterprises against malicious internet traffic and other threats from the open internet.
Defender Experts Things
Frost & Sullivan names Microsoft a Leader in the Frost Radar™: Managed Detection and Response, 2024 | Microsoft Security Blog - We are excited to share that Microsoft has been named a Leader by Frost & Sullivan in the Frost Radar™: Managed Detection and Response, 2024, leading in innovation and among the top two in growth. Frost & Sullivan highlighted Microsoft Defender Experts for XDR as a key component of Microsoft’s managed detection and response (MDR) offering, which delivers a managed extended detection and response service that triages, investigates, and responds to incidents to help organizations stop cyberattackers and prevent future compromise.
Microsoft Purview Things
Migrating from Windows Information Protection to Microsoft Purview - In July 2022 we announced the sunsetting here: Announcing the sunset of Windows Information Protection (WIP) - Microsoft Community Hub of Windows Information Protection (WIP). The last version of windows to ship with WIP will be Win11 24H2.
Seamlessly secure your data estate with Microsoft Purview - Today, we are excited to share some of the next steps in our journey to secure your data estate. In this blog, we will unpack how we are enabling customers to:
Apply built-in data security controls in Microsoft Fabric.
Establish uniform protection policies across multiple data sources.
Enhance user risk signals in Insider Risk Management.
Intro to MS Purview Information Protection – Part 1 - Azure Information Protection (AIP) is a cloud-based solution that can help organizations to protect sensitive information by classifying and (optionally) encrypting documents and emails on Windows, Mac, and Mobile devices.
New Microsoft Purview features to secure and govern your data estate | Microsoft Security Blog - We live in a world where data is constantly multiplying. According to IDC, the global datasphere, which is the amount of data created, captured, or replicated, will double every four years.1 As AI becomes more prevalent in various domains, organizations face the challenge of securing their growing data assets, while trying to activate their data to drive better business outcomes. We know data is the fuel that powers AI, but the real question is, is your data estate ready?
Microsoft Exposure Management
Microsoft Security Exposure Management, Why You Should Care -- Virtualization Review - I've enjoyed access to the private preview for some months -- in this article I'll outline what it does, why you should care and raise some still unanswered questions. I'll also look at the overall landscape of Vulnerability Management, exposure tools and the uphill battle we're all fighting to manage an ever-expanding attack surface in our organizations.
Security Exposure Management - Transform your security posture to stop attacks before they happen using Microsoft’s Security Exposure Management in Microsoft Defender. Identify and mitigate potential threats with a comprehensive view of your organization’s attack surface, critical assets, and security events. Prioritize security efforts effectively with curated initiatives, automated alerts, and actionable insights, so you can close down vulnerabilities before they’re exploited.