Things from Me
Happy Friday, everyone!
For me, the last week has been a bit frantic. I have a few trips and events coming up so that always means trying to get all things in order before embarking. And that effort can be challenging at times.
Before leaving you to this week’s newsletter content, there’s a few highlights to cover…
…
BlueHat
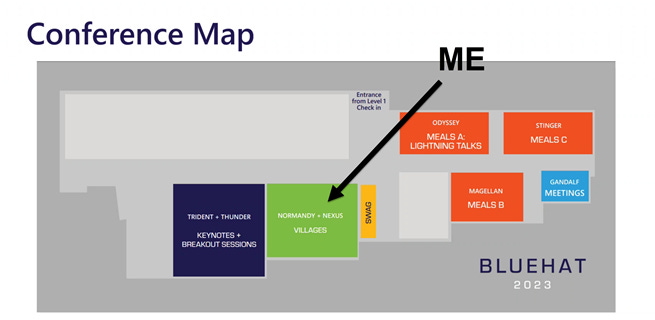
Will you be at Microsoft BlueHat next week? If so - so will I. I’ll be on-hand in Building 33 helping manage the Cyber village and traversing the hallways looking to drag attendees in. The Villages are very much what you’d expect if you’ve ever experienced these at other events like Blackhat. In fact, what we do next week at BlueHat will be tuned and honed to deliver at Blackhat (and other places) this year.
Part of the activities include playing the actual Who Hacked boardgame. Winners will be entered into a raffle to take home the boardgame package, which includes a 1st edition Who Hacked comic book!
We’ll also be raffling off signed copies of the Must Learn KQL book. And, hey…if you’re in attendance and bring your own copy of the book, I’ll sign it on the spot.
So, if you’re attending next week, I hope you’ll at least stop by to say “Hi” but definitely come by to help us test and build our Village template.
Here’s where you’ll find me:
…
Your help needed.
We would love to hear about your Microsoft Community experiences.
Please take a moment to share with us your community insights and priorities. This will help shape the Microsoft Community Advisory Board priorities for the next six months as we continue to support the Microsoft Community at large. ALL feedback welcome. Please share broadly.
Survey link: https://rodtrent.com/p8x
…
$8 Off the Microsoft 365 Security for IT Pros (2023 edition) book
Have you heard about the Microsoft 365 Security book? Written by several community experts and MVPs, this book is a fantastic, self-published tome about all things Microsoft Security. The best part is that it is constantly updated to keep pace with Microsoft’s own accelerated product cycles.
I wrote the foreword for the most recent revision of the book, so the authors have kindly offered you all an $8 discount code.
You can acquire the book from the following link: https://rodtrent.com/da9
Use the discount code: R0dR0cks
…
…
Defender for DevOps PR Annotations Adoption Survey
Defender for DevOps exposes security findings as annotations in Pull Requests (PR). Security operators can enable PR annotations in Microsoft Defender for Cloud. Any exposed issues can then be remedied by developers. This process can prevent and fix potential security vulnerabilities and misconfigurations before they enter the production stage. Defender for DevOps annotates the vulnerabilities within the differences in the file rather than all the vulnerabilities detected across the entire file. Developers are able to see annotations in their source code management systems and Security operators can see any unresolved findings in Microsoft Defender for Cloud.
If you have tested Defender for DevOps, please give your feedback regarding Pull Request annotation adoption.
Survey link: https://rodtrent.com/mcm
…
Help define Advanced Hunting
We would like to get your feedback on hunting experience to learn how we can improve. Even if you are not using Advanced hunting yet, your feedback is very valuable to us.
Survey link: https://rodtrent.com/brl
…
That’s it from me for this week.
Have a wonderful week ahead!
Talk soon.
-Rod
Things to Attend
Upcoming Spring 2023 | Microsoft Cloud Security Public Webinars
All webinars are held at 08:00-09:00 AM, PT and registration using the following link: https://rodtrent.com/syi
Jan 31 - Microsoft Defender for Cloud | What's New in the Last 3 Month's
Feb 15 - Microsoft Defender Threat Intelligence | Overview: Microsoft Defender Threat Intelligence
Feb 16 - Azure Network Security | Azure Firewall SKUs - Basic vs Standard vs Premium
Mar 15 - Microsoft Defender External Attack Surface Management (EASM) | Introduction to Microsoft Defender External Attack Surface Management
Mar 16 - Azure Network Security | Multi-cloud: Protecting GCP and AWS Applications with Azure WAF
Mar 23 - Azure Network Security | How to tune your Azure WAF
Mar 30 - Azure Network Security | Azure DDoS Protection Integration with Microsoft Sentinel
Things that are Related
Upgrade to the latest version of the Windows Log Analytics agent (MMA) by 14 April 2023 - On 14 April 2023, Azure will no longer accept connections from older versions of the Windows Log Analytics agent, also known as the Windows Microsoft Monitoring Agent (MMA), that uses an older method for certificate handling. Please upgrade your agent to the latest version by that date. We encourage you to be on the latest version of the agent. Agents that are on version - 10.20.18053 (bundle) and 1.0.18053.0 (extension) or newer won't be affected. If you're on an agent prior to that, your agent will be unable to connect, and it will break.
Azure Monitor agent extension versions - This article describes the version details for the Azure Monitor agent virtual machine extension. This extension deploys the agent on virtual machines, scale sets, and Arc-enabled servers (on premise servers with Azure Arc agent installed). We strongly recommended to update to the latest version at all times, or opt in to the Automatic Extension Update feature.
Things to Watch/Listen To
Microsoft Security Insights Show Episode 138 - Just us, probably - Our regularly scheduled guest, Ann Johnson, was sick for today’s show. We wish Ann the best and hope she recovers quickly. Ann will be joining us in March during Women in Cybersecurity month. This week we discussed a slew of stuff including: ChatGPT, AI, BlueHat, Microsoft Secure, Build, Microsoft Reactor and others.
What's New in the Last 3 Months - Microsoft Defender for Cloud - Microsoft Defender for Cloud is in active development and receives improvements on an ongoing basis. In this session, we will summarize and demo what we've released for Microsoft Defender for Cloud in the last 3 months that you need to know about.
Things in Techcommunity
Defender Policy VS Baseline Conflict: Scan network - On the defender policy section it has an option for "Scan Network Files" the options are Yes or No On the Baseline in the Defender section it has the "Scan Network Files" section as well and the options are Yes and Not Configured (which states it won't scan them if that is selected. However, This then causes a policy Conflict when rolling out the baseline to users with the Defender Policy.H as anyone found a work around on similar issues?
Microsoft Defender for Cloud | Environment settings - Question on Configuration - What exactly is difference when comes to enabling different plans against the “azure subscription” here (Azure Pass – Sponsorship) and The Log Analytics Workspace (FirstLAW), which is also under the same subscription.
Microsoft Sentinel Tech Community Join the other 64,000 members of the Tech Community to ask questions to the product team and get the latest on product updates. The Sentinel Tech Community is free to join and provides the easiest way to get notified when something new is in product, and how you can implement it into your workflows.
Defender for Cloud Things
BLOG: Automate Reporting of Defender for Cloud recommendations & Role Assignments with 35 different views - In this blog, I will demonstrate, how you can extract security recommendations from Microsoft Defender for Cloud using Azure Resource Graph – delivering a horizontal cross-subscriptions, workload overview. Data will automatically be exported into a Excel spreadsheet with 19 Excel tables and 16 pivot tables.
How to protect Azure storage accounts (Blob) using Defender for Storage - Defender for Storage is the Azure-native layer of security intelligence that detects potentially harmful attempts to access or malicious activity. With the use of Microsoft Threat Intelligence and security AI, contextual security alerts and recommendations are available. Defender for Storage is part of the Defender for Cloud stack. Cloud storage is a common target for attackers focussed on sensitive information for further exfiltration.
BLOG: A Proactive Approach to Cloud Security Posture Management with Microsoft Defender for Cloud - In this blog, I discuss the importance of proactive security posture management, how security teams can be organized for security posture management, how roles and responsibilities can be divided among the teams. I further discuss what a person with proactive security posture responsibilities needs to do and how to do it by leveraging Microsoft Defender for Cloud’s Attack Path capabilities.
Module 17 – Defender CSPM - Learn how to enable Defender for CSPM, and leverage Defender for CSPM Capabilities.
Defender for Endpoint Things
BLOG: Prevent phishing based on domain registrations - Business email compromise and phishing are just two of the threats sent to hundreds and thousands of email inboxes around the world every day. As defenders, we use various tools and methods to limit the delivery of these emails to the intended target.
BLOG: Defender for Servers - Failed MDE. VM Extension Report - Sometimes during enterprise deployments using Defender for Servers auto deployment, errors can occur with the onboarding of Azure virtual machines or Arc connected servers into Defender for Endpoint.
BLOG: Push ASR rules with Security Settings Management on Microsoft Defender for Endpoint managed devices - In May 2022, we announced the general availability of Security Settings Management for Microsoft Defender for Endpoint. This release empowered security teams to configure devices with their desired antivirus, EDR and firewall settings without needing to deploy and implement additional tools or infrastructure. Today, close to a million endpoints worldwide have received security policies through Security Settings Management, ultimately saving IT and security teams time and resources managing these policies while helping keep their organizations safer from security and data breaches in the process.
365 Defender Things
BLOG: Protect against cyber threats and improve your security posture with Microsoft 365 Defender - Did you know that the Microsoft 365 admin center includes Advanced deployment guides to help you deploy Microsoft 365 Defender products? Ensure your cloud IT environment is secure from day one with the Microsoft 365 Defender for Endpoint, Office, Cloud Apps, and Security Analyzer.
BLOG: Automate your alert response actions in Microsoft 365 Defender - While Microsoft’s Extended Detection and Response (XDR) solution helps prioritize response activities and provides a unified experience that allows for more effective investigation at the incident level, the increasing volume and speed of sophisticated attacks, still challenges the capacity of most security teams. Automation is growing in importance to close the gap to the speed needed to respond to more attacks faster. Automating the response actions to common alerts in can help you stay ahead of threats, protect your organization more effectively, significantly reduce response times, and save manual work for the Security Operations Center (SOC).
Defender for Identity Things
BLOG: Microsoft Defender for Identity Hidden Feature Customer Logs Location - Although Microsoft did not document this feature yet, it is possible to set a custom location for your log files for Microsoft Defender for Identity since sensor version 2.197. In this short blog post, I will describe how to set up a custom location for the Microsoft Defender for Identity log files.
Microsoft Purview Things
CODE: The Microsoft Purview Advanced Rich Reports (MPARR) Collector - Today have the right information in the right moment can be a great business value, we are talking about implement security and compliance, one of the most importance things are understanding that this accomplishment is a business goal, in that order of ideas, to have reports, business-friendly, to see how our end users are using and adopting these tools is a global benefit. In that order of ideas, this solution take the information available under the Microsoft 365 services and give the capabilities to present this information to different business units, given the capacity to c-level users have access to business metrics related to compliance.
BLOG: Time-based scheduler for Microsoft Purview Data Estate Insights App is now generally available - Data Estate Insights is an app built on Microsoft Purview’s platform that serves the office of the Chief Data Officer (CDO), catering to their needs for governance and curation analytics and insights. The app offers a range of out-of-the-box dashboards, that use the rich knowledge of the DataMap to create meaningful aggregates for high-level business understanding, and detailed views into the metadata, for deeper dives by Data Stewards and Data Custodians.
BLOG: Navigating Data Privacy Regulations with Microsoft Cloud - As businesses and organizations continue to prioritize data security, privacy, and compliance, they turn to Microsoft Cloud for its commitment to addressing these concerns. Our cloud services are designed with security in mind, and we adhere to industry standards for data protection. In addition, our strict policies and procedures, as well as our automated service operations, ensure that customer data remains private and secure.
Defender for Business Things
VIDEO: Microsoft Defender for Business Threat Protection Solution for Small and Mid-sized Companies - Microsoft Defender for Business is the new Cyber Protection Platform released by Microsoft to help protect the Customers from Cyber Threats.
Microsoft Entra Things
BLOG: Combatting Risky Sign-ins in Azure Active Directory - It is almost inevitable your organization will be targeted with malicious sign-in attempts to cloud apps. It is often the case an employee uses the same password for their work account as they do for their personal accounts. Password leaks from organizations other than yours pose a threat if your employees are using the same password for the same apps, even if their email/UPN is different. As more apps are moving to the cloud it becomes increasingly more imperative that these malicious sign-in attempts don’t go unnoticed and correct action is taken against them.
BLOG: Seamless application access and lifecycle management for multi-tenant Azure AD organizations - Hello friends, today I'm thrilled to announce that cross-tenant synchronization is in public preview! Your organization may have recently acquired a new company, merged with another company, or restructured based on newly formed business units. As your organization evolves, your IT team adapts to meet the changing needs. This often includes integrating with an existing Azure AD tenant or forming a new one. Regardless of how your identity infrastructure is managed, we know how critical it is that end users have a seamless experience accessing resources and collaborating across tenants. Cross-tenant synchronization enables organizations to provide seamless access and collaboration experiences in your multi-tenant environment.
Microsoft Priva Things
BLOG: Celebrating data privacy week—New Microsoft Priva features available in public preview - Data Privacy Week encourages us to learn more about protecting our privacy online, especially in a vast digital world. For individuals and organizations alike, privacy and security often go hand in hand. With ever increasing data footprints, strong awareness of online privacy is important, but handling data appropriately and respecting privacy are key.
BLOG: Data Privacy is an all-year thing - Learn more about Microsoft Priva - Data Privacy Week may have ended but Data Privacy is an all-year thing. Microsoft understands how important Data Privacy is to not only your Microsoft investments and portfolio, but to your entire data estate. Since the launch of Microsoft Priva, we have been committed to continually improving data privacy and supporting organizations on their privacy journey. Check out the new features available in public preview.
Need a new laptop sticker? Released just this past week there’s new Must Learn KQL merch! You can find this one at: https://rodtrent.com/w35
***All proceeds go directly to St. Jude Children’s Research Hospital.